-

Is WhatsApp safe to use? A complete guide for every user
WhatsApp is a pretty safe and secure messaging app. It has a suite of privacy and security features, including end-to-end encryption, two-step verification, and more. All these serve to keep your conv...
-

How to know if your phone has a virus?
If your phone is acting strangely—running slowly, draining your battery quickly, or showing unexpected ads, for example—it could have a virus. You shouldn’t ignore these signs; it only takes a f...
-

Is hotel Wi-Fi safe? How to browse securely while traveling
Free Wi-Fi has become standard in hotels all over the world, which makes it easy to stay connected while traveling. But is hotel Wi-Fi safe? The short answer is no. Many hotels don’t take the time t...
-

What is a VPN kill switch and how does it work? (+ setup guide for different devices)
A VPN masks your IP address, encrypts your traffic, and conceals your activity from third parties and potential eavesdroppers—until the moment the connection drops. That short gap is all it takes fo...
-
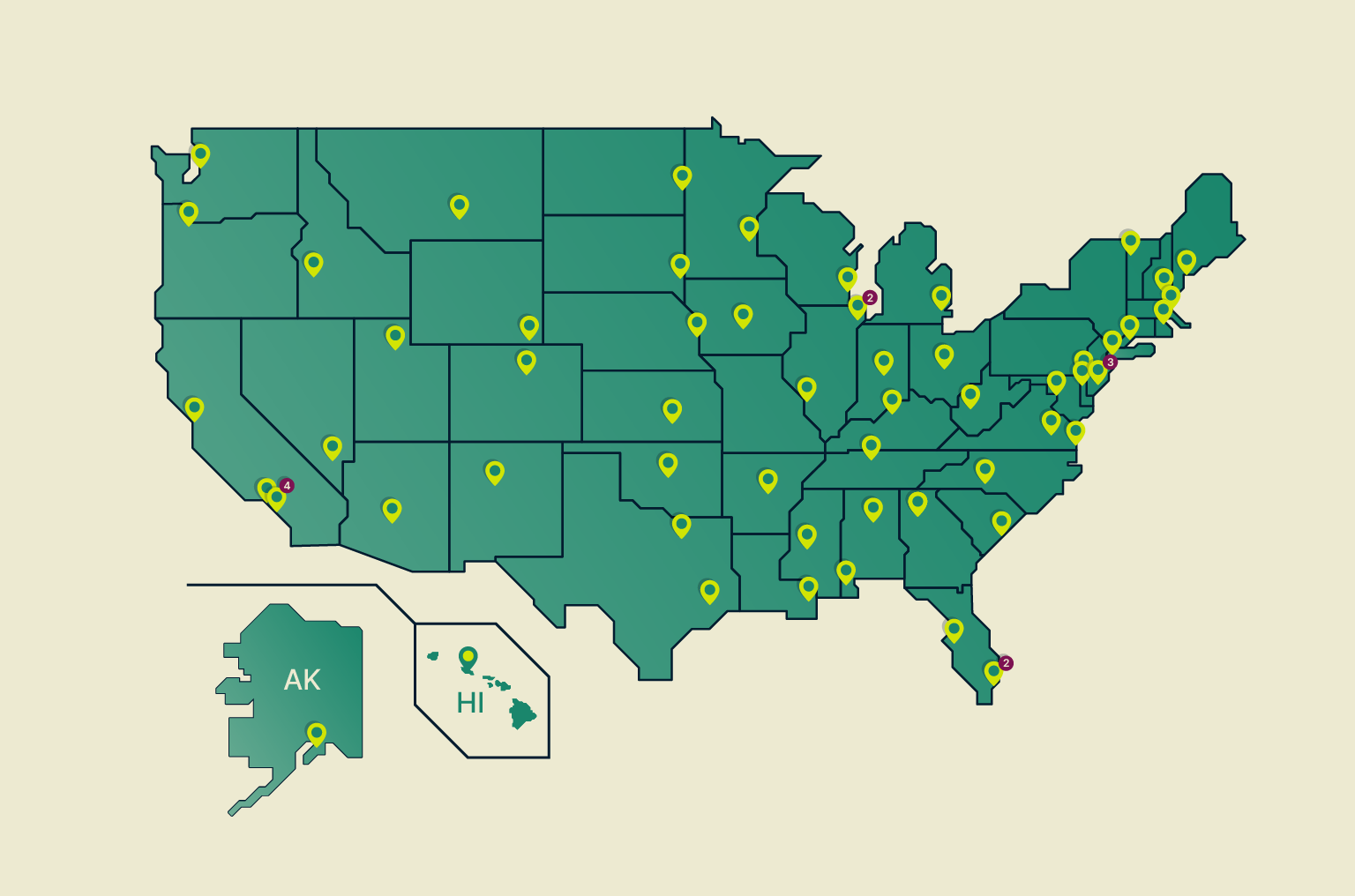
ExpressVPN now has servers in all 50 U.S. states—here’s what that means for your privacy
State laws are reshaping the internet. Rules about data collection, content access, and identity checks now vary depending on where you live. As a result, the online experience in the U.S. is becoming...
-

What does jailbreaking an iPhone do? Is it worth the risk?
You may have heard about people jailbreaking their iPhones to install unauthorized apps or customize the operating system in ways Apple doesn’t allow. While it can give you more control over your de...
-

How to secure your bank account from hackers: A complete protection guide
You can now manage your bank account from almost anywhere. Whether you’re on the couch watching TV or waiting in line at the store, online and mobile banking make it simple to deposit checks or pay ...
-

LinkedIn scams in 2025: How to spot and report them
Cybercriminals have gone corporate. From fake job offers to investment traps disguised as “opportunities,” LinkedIn scams have become sleek, professional, and surprisingly convincing. Here’s how...
-
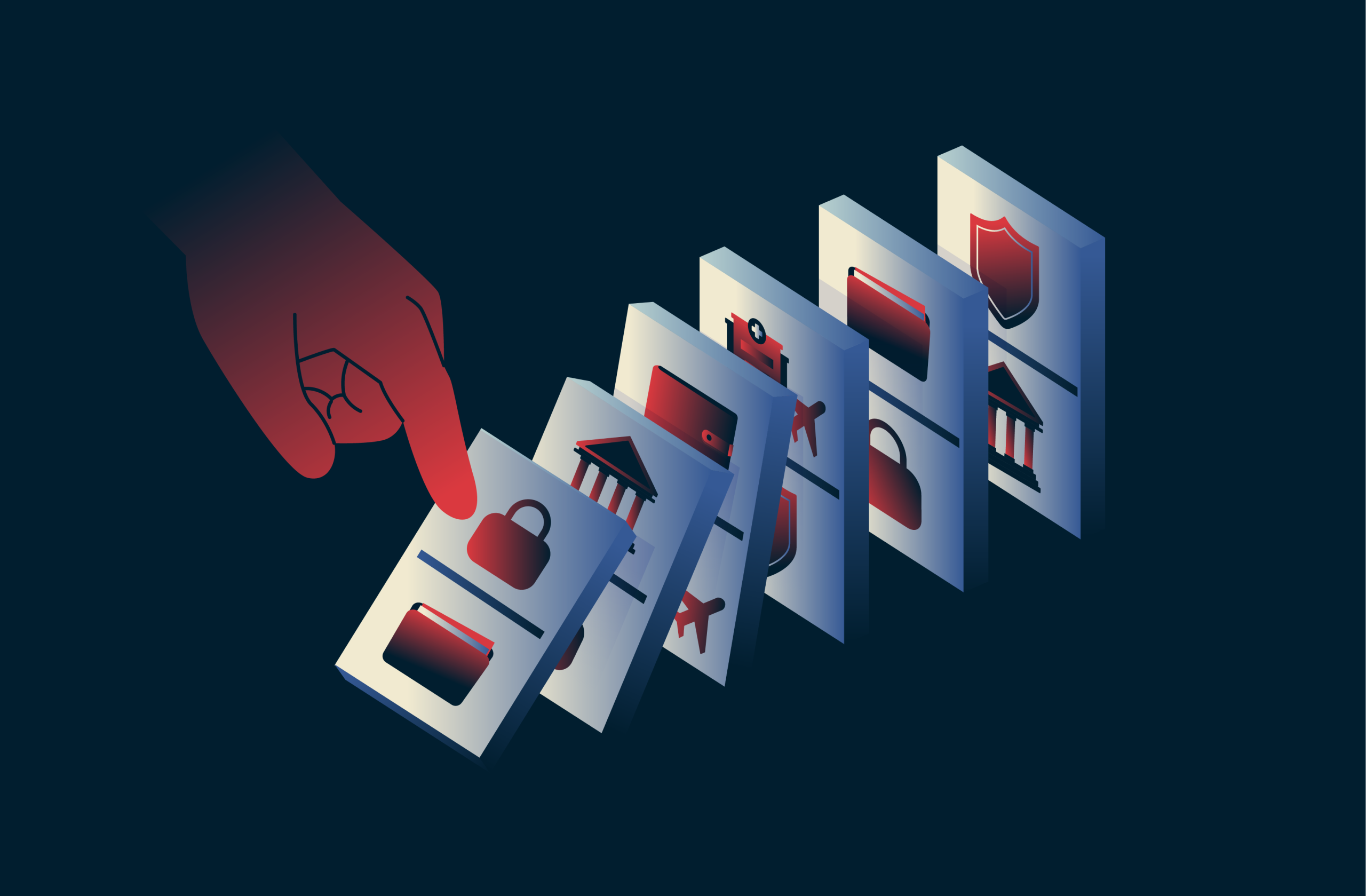
The true cost of cyberattacks in 2025 and beyond
Cyberattacks can strike in seconds but leave you paying for months. A ransom note may appear the moment attackers break in, but the real cost—instant containment, forensic investigations, legal coun...
-

What is spyware? Types, examples, and how to prevent it
Think your device is secure? It might not be as safe as you think. Spyware can quietly install itself on your system and start watching everything you do—tracking your activity, logging your passwor...
