Ingress and egress: Everything you need to know
Ingress and egress are essential for network security and traffic management. These two concepts control how data enters and exits a system, affecting everything from performance to risk exposure.
Knowing how these processes work, how they differ, and how to manage them properly can help keep your network safe and running smoothly.
In this guide, you'll get a full breakdown of ingress and egress traffic: what they are, why they matter, and best practices for managing them. We’ll also discuss common issues with ingress and egress and how they tie into your overall cybersecurity strategy.
Understanding ingress and egress
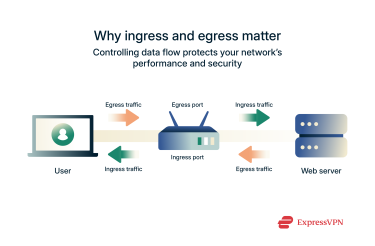
Ingress and egress describe how data moves across a network boundary. Think of it like this: when your PC sends data to your router, which then passes it to your internet provider and finally to a website, that’s egress (data going out). When the website responds, the data travels back along the same path to your PC. That’s ingress (data coming in).
What is ingress?
Ingress refers to data or traffic entering your network from outside sources, like incoming emails, website requests, API calls, or remote connections.
In cloud and enterprise networks, managing ingress is important for protecting systems from unwanted or harmful traffic. Tools like firewalls and authentication checks filter and control what gets through, helping maintain security and stability.
What is egress?
Egress refers to data or traffic that leaves your network and goes to an external destination, such as the internet or another network. This includes outgoing emails, file uploads, and responses from APIs.
In cloud environments, managing egress is critical for keeping sensitive information secure and making sure only authorized data is sent out. It also helps maintain overall network performance and compliance with data policies.
Ingress vs. egress: Key differences
The main difference between ingress and egress is the direction of traffic and the way you can control it. In essence, ingress ports manage incoming connections, while egress ports manage outgoing ones. Understanding these roles is key to configuring network devices for optimal performance and security.
When setting up ingress and egress ports, be sure that your port 443 isn’t blocked. This port serves as the backbone of HTTPS, encrypting your connection to protect it from prying eyes.
Here’s a quick overview of the differences between ingress and egress:
| Aspect | Ingress | Egress |
| Direction | Traffic coming into a network | Traffic leaving a network |
| Examples | Incoming emails, API requests, and web browsing requests | Outgoing emails, data uploads, and API responses |
| Main risk focus | Blocking malicious traffic | Preventing data leaks |
| Common controls | Firewalls, access controls, and intrusion prevention systems (IPS) | Data loss prevention (DLP) tools, egress firewalls, and monitoring tools |
| Goal | Protect internal systems from external threats | Safeguard sensitive data leaving the network |
Why are ingress and egress important?
Ingress and egress allow you to control the flow of data, which is essential for security and performance. Without proper oversight, networks can be exposed to cyber threats, data leaks, and slowdowns. By monitoring traffic, you can detect suspicious behavior, safeguard sensitive information, and keep systems running smoothly.
Role of ingress and egress in cloud computing
In cloud environments, ingress and egress traffic management is critical, as cloud platforms typically handle very large volumes of incoming and outgoing data. With ingress and egress management, you can achieve the following:
- Better cost control: Most cloud providers charge for egress (outbound) data transfers, while ingress (inbound) traffic is often free. By controlling egress, you can reduce unexpected costs associated with large volumes of outbound data.
- More reliable performance: Proper management helps maintain efficient and reliable network performance, especially as cloud environments scale and handle larger volumes of data.
Impact on data security and network management
Effective ingress and egress controls also play a key role in strengthening cybersecurity. Managing incoming and outgoing data traffic helps with the following:
- Improved security: Clear ingress and egress rules limit exposure to threats by ensuring only authorized traffic enters or leaves your cloud environment. This helps prevent unauthorized access, data breaches, and data exfiltration.
- Improved access management: Ingress and egress rules allow you to tightly control who can access your resources and where your data can go, supporting compliance and governance requirements.
Common challenges and solutions
Managing ingress and egress traffic isn’t always straightforward. As networks become more complex, especially with the shift to cloud services, it gets harder to keep track of everything coming in and going out. Here are some of the most common issues organizations run into:
| Challenge | Explanation | Solution |
| Distinguishing safe vs. harmful traffic | Malicious data can resemble normal activity, making detection difficult. | Implement deep packet inspection (DPI) and machine learning-based traffic analysis to identify anomalies. |
| Monitoring high data volumes | Cloud environments generate large traffic volumes, which makes tracking data challenging. | Use scalable, cloud-native monitoring tools for real-time traffic analysis. |
| Compliance and regulatory requirements | Industry regulations require careful management of egress traffic to avoid legal issues and fines. | Use automated compliance monitoring tools to ensure egress traffic meets industry standards. |
| Balancing security and usability | Security tools like firewalls may cause delays or make systems harder to use if they’re not configured properly. | Optimize firewall configurations and use next-gen firewalls with adaptive security policies for seamless protection. |
Ingress and egress in different environments
While the core concepts remain the same, ingress and egress behave differently across environments. In traditional on-premises networks, traffic is typically managed at a single location, giving you more direct control. In cloud environments, data can flow between various services, regions, and providers, which adds complexity to traffic management.
Each environment calls for tailored strategies to manage risk, maintain visibility, and effectively enforce security policies.
Ingress and egress in cloud networks
In cloud networks, ingress is data entering your cloud resources, like uploads or API requests, while egress is data leaving, such as downloads or backups.
Controlling egress in cloud environments
Controlling egress traffic in cloud environments is crucial for preventing data leaks and keeping costs under control. The reason is that, unlike on-premises setups, cloud providers often charge for egress traffic, so controlling it helps improve both security and cost management. Best practices include using firewalls with strict outbound rules to regulate what can leave your network.
Managing ingress traffic efficiently
Efficient ingress management begins by filtering incoming traffic at the network’s edge. Tools like firewalls, load balancers, and intrusion detection systems (IDSs) block harmful connections and direct legitimate traffic where it needs to go. In cloud environments, features such as security groups, private endpoints, and API gateways help narrow ingress points and minimize exposure to external threats.
How ingress and egress work in firewalls
Firewalls are essential for controlling both ingress and egress traffic, ensuring that only trusted data enters and leaves your network. Here's how it looks in practice:
- Ingress traffic in firewalls: Firewalls control ingress traffic by checking the source IP, port, and protocol against set rules to allow or block access. This helps stop malicious data, unauthorized access, and other threats from entering your network. Some firewalls also inspect deeper data layers for malware or intrusions.
- Egress traffic in firewalls: Controlling egress traffic is key to preventing unauthorized data from leaving your network. Firewalls control outbound traffic by blocking risky destinations, limiting file uploads so people can’t use your website to host files that unnecessarily increase your egress traffic, and ensuring data leaving the network complies with security policies.
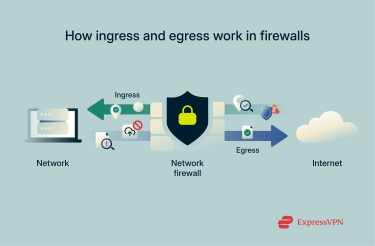
By managing both ingress and egress traffic, firewalls protect your network from external threats, maintain privacy, and prevent data breaches, while also ensuring that legitimate communication can flow smoothly.
Ingress and egress in data centers and enterprises
In data centers and enterprise environments, managing ingress and egress traffic is crucial for security, performance, and compliance. Here’s how each aspect of data flow impacts an enterprise or data center.
- Ingress: Effective management is vital to block malicious access and ensure legitimate traffic is routed properly. Tools like firewalls filter incoming traffic, while IDSs monitor for threats. Load balancers help distribute traffic efficiently, and VPN gateways secure remote access.
- Egress: Managing egress helps prevent sensitive data from leaking and ensures only authorized data exits the network. DLP tools block unauthorized data transfers, while egress firewalls restrict outbound traffic. VPNs and private links secure outgoing data, and network monitoring detects any unusual transfers.
Managing both directions can be complex, especially at scale. Best practices include using network segmentation, continuously monitoring traffic, and adopting zero-trust principles to secure every connection.
Ingress and egress in VPN networks
A VPN plays a key role in protecting your data by managing both ingress and egress traffic to maintain privacy, security, and reliable performance. However, it’s important to know that VPNs and firewalls are two different security measures, each serving a distinct purpose when it comes to protecting your data.
How VPNs handle ingress and egress traffic
VPNs protect data on both ends (what comes in and what goes out) by encrypting traffic and routing it through secure servers. This helps shield sensitive information from surveillance, interception, or tampering, whether it's incoming or outgoing.
Keep in mind that a huge VPN server count doesn’t necessarily mean the service is fast or capable of handling large volumes of ingress and egress traffic. There’s more to performance than just numbers; factors like server quality, network infrastructure, and load balancing matter, too.
ExpressVPN offers ultra-fast 10Gbps servers (with many upgraded to 40Gbps) that protect your ingress and egress traffic with 256-bit Advanced Encryption Standard (AES) encryption. The VPN also comes with perfect forward secrecy, which regularly changes the encryption key. So, even if a portion of traffic were somehow exposed, an unlikely scenario thanks to features like kill switches and leak protection, it would be extremely difficult to decrypt.
VPN egress: Encrypting outbound traffic for privacy
VPN egress involves encrypting all outgoing data. This encryption typically occurs on the client side. It hides your IP address, preventing internet service providers (ISPs), hackers, or any other third parties from monitoring or tracking what you do online. Additionally, it ensures that data, whether from browsing, streaming, or communication, stays private and secure as it leaves the network.
VPN ingress: Filtering incoming traffic for security
On the ingress side, when data enters a VPN network, it’s encrypted and sent through the VPN server to its destination, whether it’s a website, app, or another service.
This helps protect you from malicious inbound traffic and prevents cyberattacks, like man-in-the-middle attacks, from compromising data as it enters the network.
Best practices for managing VPN traffic flow
If you're setting up your own VPN, something you can do by following this guide, or using a commercial one that follows best practices, you can help ensure that traffic is managed securely and efficiently, keeping your network protected and performance optimized.
| Best practice | What it does |
| Use VPN tunneling wisely | Route only specific traffic through the VPN to optimize performance, but avoid exposing sensitive data outside the VPN. |
| Monitor for unusual traffic | Regularly track ingress and egress traffic for anomalies using IDSs and logging tools. |
| Prioritize critical traffic | Prioritize important traffic to ensure minimal latency for critical apps. |
| Optimize server locations | Choose geographically close servers to reduce latency and improve VPN performance. |
| Enforce strong encryption | Use robust encryption protocols like ExpressVPN’s Lightway, OpenVPN, or WireGuard to secure data as it enters and leaves the network. |
| Enable kill switches | Use kill switches to block egress traffic if the VPN connection drops, maintaining security. |
| Keep software updated | Regularly update VPN software to patch vulnerabilities and improve performance. |
| Balance server load | Distribute traffic across multiple VPN servers to prevent congestion and improve performance. |
Security risks related to ingress and egress
If not properly managed, both ingress and egress traffic pose security risks. Poor control over either can lead to data breaches, system vulnerabilities, and exposure to cyberattacks. For instance, weak ingress controls can let malicious traffic in, while unregulated egress traffic can lead to data leaks or unauthorized access to sensitive information.
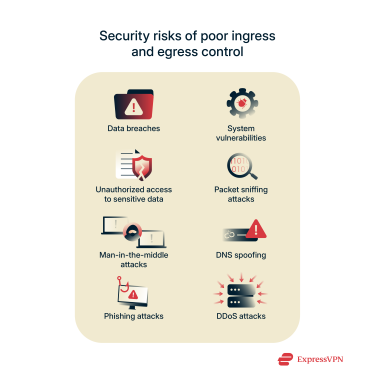
Data interception is also a risk; cybercriminals can capture data as it enters or leaves the network using techniques like packet sniffing, man-in-the-middle attacks, or DNS spoofing. Phishing attacks are another threat, as they can trick users into revealing sensitive information like login credentials or payment details, which can then be used to infiltrate systems.
Additionally, distributed denial-of-service (DDoS) attacks can overwhelm systems with traffic, rendering them slow or completely unavailable.
Poor egress control allows sensitive data to exit the network without authorization. This can happen when outgoing traffic isn’t properly encrypted or when access to certain data is not restricted.
Cybercriminals may exploit this weakness to exfiltrate data, leading to breaches or intellectual property theft. Without effective monitoring, malicious users can also send data to external servers unnoticed.
Preventing unauthorized ingress traffic
Unauthorized ingress traffic refers to unwanted or malicious data trying to enter your network. To prevent this, here’s what you can do:
| Measure | Purpose |
| Filter incoming traffic | Allows only trusted data sources to access your network |
| Block suspicious IP addresses | Prevents known malicious actors from reaching your systems |
| Use a firewall | Blocks or mitigates harmful traffic in real time |
| Update and patch systems regularly | Closes security vulnerabilities that attackers could exploit |
| Enable proper access control/authentication | Ensures people can only access what they’re authorized to |
| Deploy an IDS | Monitors and alerts you to suspicious network activity |
Best practices for managing and securing ingress and egress traffic
Before you start managing your ingress and egress traffic, it’s a good idea to remind yourself of technical terms using our glossary. With that said, here’s what you should do to optimize and secure your network.
- Filter traffic with firewalls: Use firewalls to inspect and filter both ingress and egress traffic, blocking harmful or unauthorized traffic while allowing legitimate data.
- Encrypt data in transit: Ensure all data entering and leaving your network is encrypted to prevent interception by malicious actors. The easiest way to do it is to install a VPN and use split-tunneling to route any sensitive traffic through it.
- Regularly monitor traffic patterns: Implement traffic monitoring to detect abnormal behavior or potential security threats, like sudden spikes or unusual destinations.
- Establish access controls: Apply role-based access control to limit who can send and receive data, ensuring only authorized users have access to sensitive information.
How to monitor and control data egress?
Monitoring and controlling data egress (the flow of information leaving your network) is essential for preventing leaks, complying with regulations, and keeping sensitive information secure.
One of the most effective ways to manage this is by using DLP tools. These systems help you track sensitive data and prevent it from leaving your network without proper authorization. Whether it’s customer information or internal documents, DLP tools ensure the right controls are in place.
It’s also smart to set clear rules for where data can go. For example, you can block access to untrusted external servers or limit file uploads to specific, approved destinations. This kind of traffic control reduces the chance of data ending up somewhere it shouldn’t.
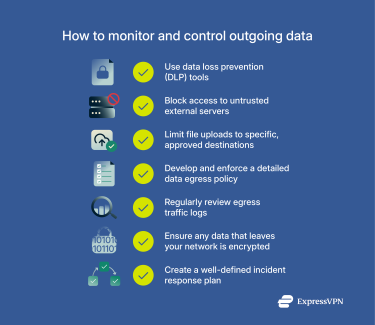
To support this, organizations should also develop and enforce a detailed data egress policy. This policy should clearly define acceptable data use, list approved internet-accessible services, and explain how employees should access and handle sensitive information. A firm policy helps standardize practices, protect critical resources, and reduce the risk of accidental or intentional data exposure.
Another important step is to regularly review egress traffic logs. These logs can highlight signs of unusual behavior, like large data transfers or attempts to reach blocked locations, both of which could signal a security issue. Additionally, make sure any data that does leave your network is encrypted. That way, even if it’s intercepted, it stays protected and unreadable to anyone without the proper keys.
Finally, organizations must actively prepare for potential breaches. A well-defined incident response plan plays a critical role; it assigns responsibilities, lays out step-by-step actions, and enables teams to respond quickly and effectively during a security event. With a strong plan in place, teams can limit damage, contain threats faster, and investigate the incident thoroughly to learn from it and reinforce future defenses.
How to optimize ingress for better performance?
To optimize ingress traffic for better performance, businesses can take several steps that reduce latency, increase speed, and maintain security, including:
- Use load balancing: Spread traffic across multiple servers to avoid slowdowns and keep things running smoothly.
- Prioritize important traffic: Set rules to prioritize critical data like video or voice calls, even during busy times.
- Select optimal server locations: For enterprises and businesses, place servers close to users to reduce delays and speed up incoming traffic.
There are several free and open-source tools that can be used to analyze ingress and egress, each offering different features to help monitor and secure network traffic. These include:
- Wireshark: This is a powerful packet analyzer that allows you to capture and inspect network traffic in real-time. It’s commonly used for troubleshooting network issues and monitoring both ingress and egress traffic, providing deep insights into packet-level details.
- Ntopng: Another open-source network traffic probe that provides a web-based interface for monitoring network traffic. It can analyze both ingress and egress traffic, offering real-time analytics, flow-based data visualization, and detailed metrics for different network protocols.
- Suricata: This is an IDS/IPS and network monitoring tool that can analyze both ingress and egress traffic. It supports DPI and can be integrated with other tools for enhanced threat detection and traffic analysis.
These tools can be used alone or together to provide a comprehensive view of network traffic. You can also use them to identify performance bottlenecks, detect potential security threats in ingress and egress traffic, and block malicious activity and unauthorized access.
FAQ: Common questions about ingress and egress
What is the main difference between ingress and egress?
The main difference between ingress and egress is the direction of traffic. Ingress refers to incoming traffic: data that enters a network or system from external sources. Egress refers to outgoing traffic: data that leaves the network or system and is sent to external destinations. Both are essential for managing network flow, performance, and security.
What is the difference between ingress and egress ports?
Ingress ports are used for incoming traffic, which is data that enters the network or device. When data is received from external sources, it passes through the ingress port. Egress ports, on the other hand, handle outgoing traffic (data that leaves the network or device). When data is sent to external destinations, it exits through the egress port.
How does ingress filtering prevent cyber threats?
Ingress filtering helps prevent cyber threats by blocking malicious or unauthorized incoming traffic before it enters the network. It works by inspecting and filtering data packets at the network's entry point (ingress port), allowing only legitimate and safe traffic.
This method helps defend against various threats, including denial-of-service (DoS) attacks, malware, and unauthorized access attempts. Ingress filtering examines incoming traffic for suspicious patterns, invalid IP addresses, or known attack signatures. It blocks harmful traffic before it can cause damage, helping to keep the network secure and protected from external threats.
How does egress filtering help prevent data leaks?
Egress filtering is one of the best methods to keep your network secure. It helps prevent data leaks by controlling and monitoring outgoing traffic, and it inspects data packets leaving the network to ensure that sensitive data isn't transmitted outside. Egress filtering can also detect and block attempts to send confidential data, like intellectual property or personal information, to unauthorized external destinations.
This approach helps prevent both accidental and malicious data leaks, such as when employees or attackers try to exfiltrate sensitive data. By setting up rules and monitoring outgoing traffic, organizations can ensure that only approved data leaves the network, minimizing the risk of data breaches.
How can I improve ingress and egress security?
To strengthen ingress and egress security, you need to manage the flow of data coming into and leaving your network. For ingress, use firewalls, intrusion detection systems (IDSs), and access controls to block malicious traffic and limit access to trusted devices. Keeping security protocols up to date and segmenting your network also helps reduce the risk and impact of breaches.
On the egress side, tools like data loss prevention (DLP) systems help monitor and restrict sensitive data from leaving without permission. Set egress filters to block risky external connections, encrypt outbound traffic, and review logs regularly to catch suspicious behavior.
What role do firewalls play in ingress and egress management?
Firewalls control the flow of traffic entering and leaving a network, playing a crucial role in ingress and egress management. For ingress traffic, firewalls inspect incoming data packets and filter out potentially harmful or unauthorized traffic before it can enter the network. They act as a barrier, blocking malicious sources, such as hackers or malware, from gaining access to your systems.
For egress traffic, firewalls can be configured to prevent unauthorized or sensitive data from leaving the network. They monitor outgoing traffic to ensure that only legitimate, authorized communication takes place, helping to prevent data leaks and exfiltration.
How does a VPN impact ingress and egress traffic?
A VPN secures both ingress and egress traffic by encrypting data and masking IP addresses. It protects incoming traffic from interception or tampering and shields outgoing data from tracking by internet service providers (ISPs) or hackers. By routing all traffic through its own secure servers, often located in different geographic regions, a VPN creates a secure tunnel between your device and the internet.
Are ingress and egress different in cloud vs. traditional networks?
Ingress and egress traffic behave differently in cloud networks compared to traditional setups, mostly due to how the network architecture is built. In traditional networks, data moves through centralized routers and firewalls as it enters or leaves a fixed, on-premise environment. Security is typically managed at the perimeter, with clearly defined boundaries.
Cloud networks are more dynamic. Traffic can enter from or exit to various global locations, and there’s no single entry or exit point. Instead of fixed devices, cloud environments use tools like virtual firewalls, security groups, and encryption to manage traffic. This distributed nature requires a different approach to securing both ingress and egress flows.
How do ingress and egress affect bandwidth usage?
Ingress and egress traffic directly affect bandwidth, as they include all incoming and outgoing data. Ingress uses bandwidth when receiving data, like downloads, video streams, or cloud syncs, especially with multiple active devices.
Egress traffic, on the other hand, consumes bandwidth when data is sent out. Uploading files, sending email attachments, or syncing with cloud services all contribute to outbound load. High levels of either type can cause congestion, so monitoring and managing both is key to keeping your network running smoothly.
How can I monitor ingress and egress traffic?
Monitoring ingress and egress traffic is critical for network performance and security, and a range of tools are designed to help. For incoming traffic, firewalls, intrusion detection systems (IDSs), and network analyzers let you inspect data as it enters the network. These tools can identify suspicious sources, detect anomalies, block harmful activity, and provide insights into packet flow, bandwidth usage, and access attempts.
On the egress side, tools like firewalls, data loss prevention (DLP) systems, and traffic analyzers track what’s leaving the network. They’re useful for spotting unauthorized data transfers, identifying risky connections, and making sure only approved data is sent out.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN